Cyber Security: What Should Companies Do?

This article is the second Cyber Security article, focused on IT Management concerns.
On our first article Cyber Security: Thinking Like a Hacker, we explained the necessary five strategies to have a strict security policy.
In this article, we continue with more technical cyber security recommendations.
When you consider Cyber Security principles for your company, Zero Trust and Segmentation/Isolation are the two key paradigms you need to use.
6.Question Everything
As I’m frequently mentioning, “Do not absorb someone else’s reality, question everything to create your own reality”
For example:
“Rival firm uses that Firewall. Let us do the same”
or do not think as;
“The backup solution of our rival is still in tape libraries, we need to do the same.”
Sometimes Sells Personnel would tell you, “they might know something about it.” and they give you an example which they technically have no clue about;
“Our product is the world leader in its’ field. IBM, HP, Google also use the technology that we use.”
Do not say, “They surely have asked before me” and ask the question. Do not accept irrational answers for the questions you have in your mind.
Let questioning everything always be your guiding light.
7.Secured Remote Working
Many research sets forth that after Covid-19, the business structures have turned into remote working all around the world. This is the new normal from now on, that structure will never go back as it was before the pandemic.
That’s why establishments should build their informatic substructure based on the scenario as if their employees have been working remotely and should continuously be online.
In the last 15 years, I have worked in companies designed to work remotely, and also I have created some remote working methods of my own.
Based on my experience, the first thing I would say about this subject is:
“If you want to work remotely, the most crucial step you should take is to transform from Office-Centered structure to Cloud-Centered structure”.
After all, the service procurement models are being evolved for a while from Local orientation to cloud platforms. As you can see on the chart stated as below, three models provide the services given in IT substructure;
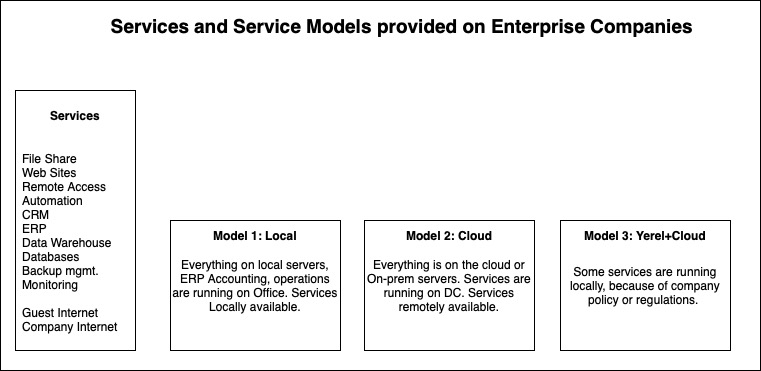
In an office-centric structure, users can easily connect the system, including ERP, over the local network and text to each other or can exchange files.
For many years, The office environment has been considered as the most secure environment to work. The visitors could connect to the internet independently from the company’s network via wireless internet.
Almost for ten years, this attitude has been slowly abandoned. However, just introducing new DMZ networks is not a feasible solution. As seen on the Isolated Approach on tableau below, there is a need for more extensive segmentation.
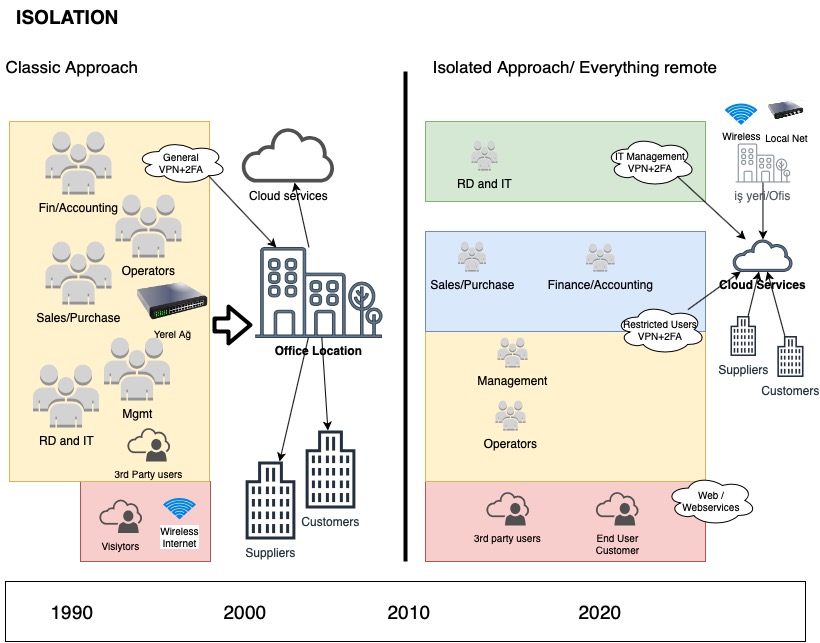
In all connections that provide remote access and links inside the company, VPN and 2FA are the most critical instruments. As you will see in the chart above, employees must use VPN to connect the systems both in or out of office.
Zero Trust
Assume all remote devices as unsecure Zero Trust
Providing security to the remote device and to patch becomes very difficult and sometimes very problematic to remote devices. Especially for the one that works in ServiceDesk, doing a very simple password change will become a huge operation.
The methods used today for managing the remote devices are neither simple nor sustainable. It contains serious risks which can increase Attack Surface.
Installing Antivirus, Domain Control, Policy and Application Management can help to secure remote devices to a certain point.
However, I believe that the best method is not giving admin rights to any remote client. Remember that the connected remote devices are the easiest inventories that can be compromised.
VDI solutions
I believe VDI environments are a must for a more secure and managed environment.
There are two different VDI approaches in the market:
- Desktop virtualization
- Bastion/Jumphost
Desktop Virtualization
In the market you have solutions like Linux Desktop/MS Terminals/Citrix VDI, what you need to do it? you need to find a good partner and make a real POC. The right partner will tell you the weak points of the VDI solutions, and you can decide what kind of solution you want to implement.
Do not make your decision via checking the Demo environments. POC is a mandatory requirement for this kind of investments. Most popular and mature platform is Citrix; alternatively, I would highly recommend you to check Linux environments.
Bastion/Jump host
Unluckily there is not software to use in the market. After the VPN connection, you will be able to reach all servers. the system manager cannot pursue your work’s follow-ups and the changes you have done in systems.
As Nucleuss, of which I am the founder, we are preparing an opensource solution for this issue. All system administrators that has access to the systems, and the devices they will use will be defined. In this way, they will be fully isolated on their operations.
8. Isolation
As mentioned in our previous article, you should learn to think like hackers and plan your entire infrastructure according to the system’s vulnerabilities.
The isolation principle divides your systems into islands. This principle will isolate the failing part in any possible attack.
“Your eggs will not be on the same basket”
Isolation is a principle that needs to be used on all designs. Besides security Isolation is crucial on design phase of Incident management, Business continuity, Backup management.
If the systems are created on isolated silos, you can control the connections on each isolated structure. In case of having an issue, alternative solutions can be easily created.
Check the diagram below named as Isolation of Services. While setting up your systems, you should do a segmentation, as stated in the diagram, and link service silos to each other.
Do not forget:
“Network segmentation increase will affect attack surface to decrease”
You can see the Attack Surface term clearly on the diagram.
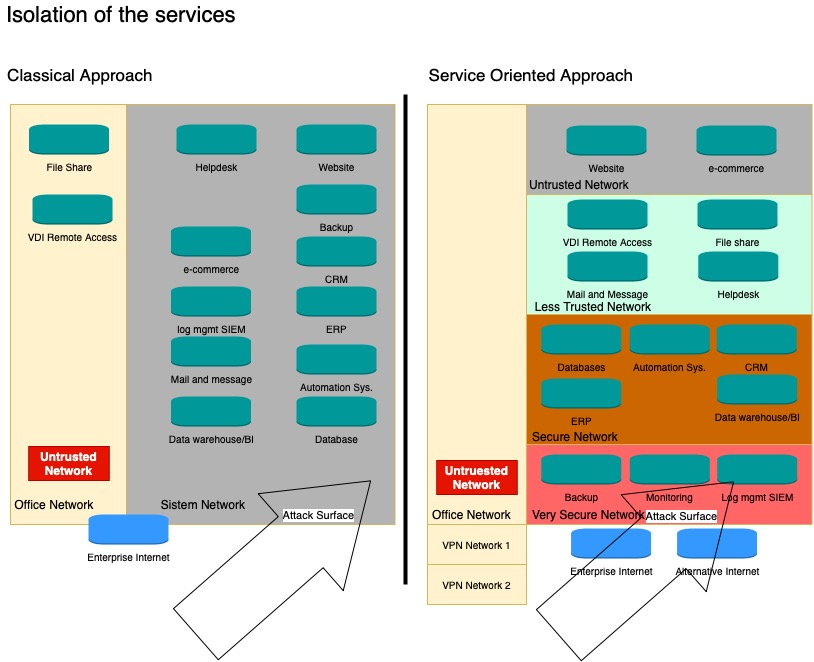
The diagram is representative; you have to redesign it in your setup.
Issue Management
Prepare scenarios such as one day the attackers will reach your services, one of the user’s laptop will be stolen, or a furious employee wants to harm you.
If you could apply Isolation principles in your systems properly. In that case, you can isolate the incident, and by analysing your isolated structure, you can see which data have been compromised and how big the damage is.
Have a detailed plan, what you will do in case of an incident. Specify the steps and tasks one by one which you will be doing in your security breach. For example, such a cleartext password comes in an e-mail. This is an incident, you need to plan for changing the whole passwords and controlling the SIEM and logs.
Business Continuity
Business continuity is a document which describes the work to be done in an emergency in a really detailed way.
In an emergency, you need to configure the processes and isolated structures of your company based on business continuity.
For instance, there is a security breach on your Web platform. In such a case, if you have a business continuity and security document, after the damage assessment, you would have an action plan for how to return to your backups.
In your business continuity document, you have to define how to connect isolated structures and who will be in charge of it.
Yet, I know a company which could not operate for five days. Because of the CEO took the key of safe while having his annual leave. (Backup tapes were in the safe)
Create a process that you define the details of business continuity.
Red Button
Sometimes having a not functioning system can be better than a working system.
This “Red Button” term, we started to hear frequently. It states the decision of pausing the live/production systems. In case of a severe problem or any security breach.
In your business sustainability document, it has to be stated clearly that which are the Red Button situations. Which will include who has the authority, and what are the processes after that.
Backup Management
If hackers hacked your system and you didn’t notice, the attackers might have already encrypted the backups that you saved for a long time. Therefore Backup Frequency is vital.
To have a backup which you can restore anytime;
Take your backups weekly, and monthly. Especially keep the monthly backups for two years on a different media.
Backups are real as much as validated by Restore Tests
Backup systems, particularly when Restore tests have not been made, can be very vulnerable and unreliable. With backup units, I have seen backups that cannot be restored, many times.
Today there are many solutions producing business continuity and backup management. While you are planning your backup systems, examine products that offer innovative solutions such as Veeam.
The essential parameter in the features that products offer should be isolation. You should copy the data which has been backup isolatedly to remote or alternative media at regular intervals.
Configuration Backups
One of my friend told me once,
“our firewall is HA and Active/Passive, why would anything happen? The Configuration backup is on the passive one…”
had a bad luck with electricity and all the firewall configs were gone. His company couldn’t operate properly for two weeks, and it took too long for their in-house automation to make their oversea connections to activate their production line.
I strongly recommend you to take the subject “Configuration Backups” seriously. Create a separate config backup solution which is integrated to your backup management.
By creating a central backup server and connecting a version control software (gitlab, gitea) with automation software such as Ansible, you can keep configurations backups easily on your own.
For the ones that use Linux, I have the following silver bullet advise:
In Linux servers the size of /etc directory is around 50 MB. This magnitude doesn’t change even you backup daily. At least copy the folder in the server as /etc2. That can be a lifesaver in some situations.
Log management software (SIEM)
(Security information and event management)
I recommend you to use a platform which you can see all kinds of logs you have. You can write alert rules that can be triggered with log events.
In this way, the information that a user is connected from many different IPs and locations can alarm you. I highly recommend you to collect your logs in the central location for security and retrospective analysis.
I have already interfered with hacked servers. Usually, the first thing we notice are the log files being deleted.
Also, SRE and DevSecOps practices tell you to manage your log and configurations as central.
As a solution, you can choose Splunk or ELK. I prefer the ELK platform because it can be used multifunctional and is open to integration with other tools.
9.Social Engineering
Social Engineers focus on solving people, instead of solving how the systems are working. They try to take possession of essential information with many kinds of tricks.
They are basically the engineers of fraud.
Social engineering is still the most popular and easy method of system hacking. Because it does not require reading dozens of books and solving how systems work via reverse engineering them.
The first person introduced the importance of social engineering is Kevin Mitnick.
Hacker’s 99% prefers to use social engineering to hack target systems, which is easier than attacking firewall systems.
There is a significant need to talk about this subject. Unfortunately, I won’t mention these topics in this article. However, to protect yourself, I highly recommend you read articles for social engineering and protection.
Some Advice to be protected from Social Engineers
- Do not write your passwords on paper.
- Use complex passwords
- Do not use the same password more than one place
- Use a password manager.
- Do not pronounce your passwords out loud to other people.
- Do not display your e-mails automatically on your computer.
- Do not share rustworthy information with someone that you don’t know and who has reached you by phone (such as the names of company servers)
- Do not tell the security violation you had on the last day to anybody.
The Last Security Violation happened on Twitter.
As it is known by the security violations that happened before, the system moderators work in Twitter connects to the systems without any VPN or 2FA.
A 17 years old boy, who knows about this vulnerability. He first searched the name of the Twitter services desk employee on Linkedin profiles. Later examine the relationships of these people on each other, from their Facebook and Twitter accounts.
By calling one of the twitter employees, he aimed and said;
“I am calling from the Twitter Support desk how are you? James told me what you did the other day in billard, Wow.”
After he got trust of the Twitter employee, he continued and hooked on as;
“In your password, there are two numbers written one after another. You need to change it.”
After that, the Twitter employee replied to him by saying,
“How can that be possible? My Password is XY1f4=4”
The boy who had this password sold it in IRC channels by saying; “I am a twitter employee, I can hack any account that you want.”
Regarding the information I have read on the internet, I wrote the above script.
It is not hard to guess what happened. I have met employees, even general managers, who give a password to here and there in similar situations during my work life.
What is very painful here is the moderators of a Tech. Giant like Twitter, don’t access their systems through VPN or 2FA.
Think of it this way and imagine what a great danger we are in ;
If the boy who hacked Twitter declared war against China from Trumps’ account, what could have happened in a couple of hours?
Additional precautions not to be forgotten
The facts I stated below can be a lifesaver from time to time.
VPN (IPs ec, L2TP, openvpn, EVPN) ve 2FA
To monitor people, you will gain access and identify the access constraints; you need to connect them with an isolated tunnel. For that in your setups, there must be VPN and 2FA. What happened with Twitter is entirely due to lack of this.
Firewalls are not a Loadbalancer! (isolation)
Using the extra features on firewalls mostly creates a problem for you. Most of these features have been put to bid on and do marketing.
By turning on this kind of feature on a Firewall, you get open to DDOS and WAF attacks.
The people who test the systems’ weakness understand firewall CPU creates 100% load when WAF you have used makes three complicated Requests. Do not forget that!
Single-purpose servers
Instead of a single server where you can create multi-purposed service for your systems, use different servers that provide only certain services.
As an example, do not use mail servers to share a file.
Or do not host your website over LAMP Server. If you do that, you created a severe impact area. At the end of the day because of a security breach on one stack will affect your other stacks. You will be creating hotspots with your hands.
The below graphic is showing tools that can be applied from most secured architecture to a less secure architecture.
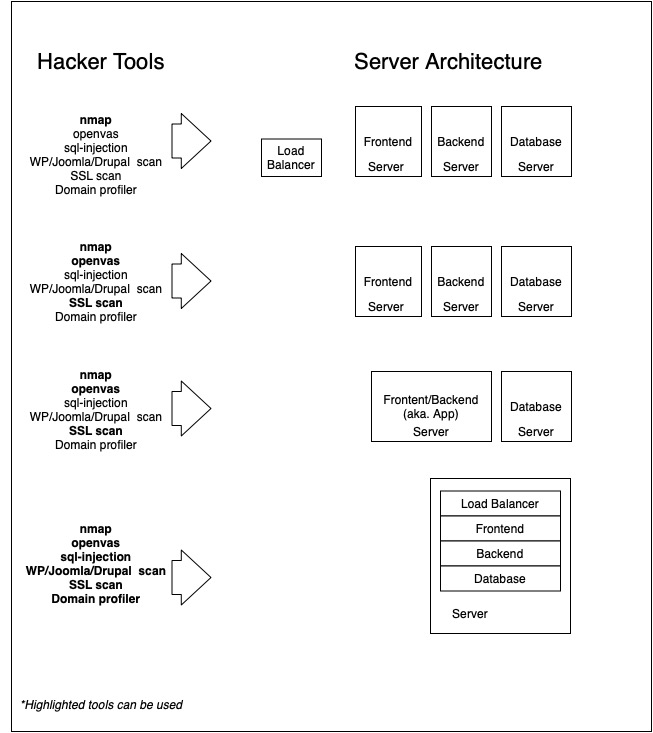
The security gap that may occur on the LAMP server will provide access to the whole system.
Logging all the access and 100% monitoring
Collect your logs on central servers by observing continuous updates and time synchronization.
Activate the netconsole feature in your Linux servers and provide your logs to an isolated environment by only giving write access.
(Above in the chart LOG server is in the securest network.)
Inventory Management (Software hardware and version tracking)
When the word inventory is used, usually only hardware is being thought. That is a deadly mistake that happens a lot. You should follow the versions of the hardware that you use. You should also have a lifecycle on the softwares that you manage.
There are many devices that you can use for Softwares patches and patch followers. If you don’t use any software, then I recommend you to use Ralph 3 open-source software.
Penetration
I advise you to test your security process professionally once a year.
Penetration tests will help you to see the weakness and strengths of your process. The frequency of tests doesn’t have to be yearly.
The important thing is to make tests before annually updating the Security Document. This way, you can add the corrections that you made to the new document. I would recommend a penetration test to companies at most every two years.
It is essential to get support for social engineering and in processual terms from the company that you will buy penetration tests. You know the processes in your company, and you might not question the truths. A third eye would be asking you the right questions about this subject.
E-Mail Groups and Security News (Mail-list and subscriptions)
Do the follow-ups of the security vulnerabilities of the software you use and track them very strictly. There are blog sites prepared for security by CVE and MS. By subscribing to them for free, you can quickly solve this issue.
Additionally, by having good relations with the ERP company that you are using, get constant information about the new security updates.
Some websites related to security which you can get benefit from;
Bonus Content,
Draft Corporate Security Document is on the link.
What should IT Manager do?
An IT manager should generate a “Corporate Security Document” based on the company’s needs, and he/she should benefit from the references to the “Information and Communication Security Guide.”